3.1 Understanding Digital Assets
Learning Objective: Clearly define digital assets and understand their primary forms and classifications on the blockchain, as well as their diverse uses.
What are Digital Assets?
Digital assets are defined as assets that exist in a digital form, can be owned and controlled, and possess economic value. In the context of blockchain, digital assets specifically refer to those created, issued, and managed based on blockchain technology. Their ownership records, transaction histories, and related rules (defined by smart contracts) are securely and transparently recorded on a decentralized blockchain ledger.
Classification of Digital Assets (Overview)
Digital assets can be classified into various types based on different dimensions:
- 暗号通貨: This is the most well-known type of digital asset. They are native tokens of specific blockchain networks, typically possessing currency properties.
- Mainstream Coins: For example, Bitcoin (BTC), known as “digital gold,” primarily serves as a store of value and medium of exchange; Ethereum (ETH), the fuel of the Ethereum blockchain, is used for paying transaction fees (Gas fees) and is foundational for DeFi and NFT ecosystems.
- Altcoins: Refers to all cryptocurrencies other than Bitcoin, which vary widely in function and purpose.
- ステーブルコイン Cryptocurrencies designed to maintain price stability, typically pegged to a relatively stable asset (like the US dollar or euro) or commodities (like gold). Examples include USDT (Tether), USDC (USD Coin), and DAI. They serve as trading mediums and hedging tools in the crypto market.
- ノン・ファンジブル・トークン(NFT): Tokens representing ownership of unique, indivisible digital or physical assets. Each NFT has unique identification information and metadata. Common applications include digital art, collectibles, in-game items, virtual land, domain names, and membership credentials.
- セキュリティトークン: Digital tokens representing ownership or rights to traditional financial assets (like company shares, bonds, real estate shares, and fund shares). The issuance and trading of security tokens are subject to strict securities regulations and compliance with KYC/AML requirements.
- ユーティリティ・トークン: Tokens that grant holders rights to access specific blockchain projects, products, services, or network functionalities. They are typically issued during Initial Coin Offerings (ICOs) and do not represent ownership in the issuing company. For example, Filecoin (FIL) is used to pay for decentralized storage services.
- Governance Tokens: Tokens that grant holders voting rights over the development direction and parameter modifications of a blockchain protocol, DApp, or DAO. Examples include Uniswap (UNI) and Maker (MKR).
Uses of Digital Assets
Digital assets have a wide range of applications and continue to expand as technology evolves:
- Payments and Value Transfer: Facilitate fast, low-cost, borderless peer-to-peer value transfers, especially advantageous in cross-border payment scenarios.
- Store of Value: Certain digital assets (like Bitcoin) are viewed by some investors as a store of value similar to gold due to their scarcity, decentralization, and anti-inflation potential.
- Investment and Speculation: The high volatility and potential returns in the digital asset market attract numerous individual and institutional investors for trading and investment.
- Participation in Decentralized Finance (DeFi): Used for lending, liquidity provision (mining), staking, and trading derivatives within DeFi protocols to earn returns.
- Access Rights and Network Participation: Utility tokens provide access to specific services, while governance tokens grant holders power to participate in project governance.
- Asset Tokenization: Converting real-world assets (RWA) such as real estate and artwork into on-chain tokens to enhance their liquidity and divisibility.
- Identity and Credentials: NFTs can represent digital identities, educational certificates, and memberships.
3.2 Digital Asset Trading Platforms
Learning Objective: Gain a deep understanding of the operational models, core functions, advantages, and disadvantages of centralized exchanges (CEX) and decentralized exchanges (DEX), and learn how to choose the appropriate trading platform based on individual needs.
Centralized Exchanges (CEX) vs. Decentralized Exchanges (DEX)
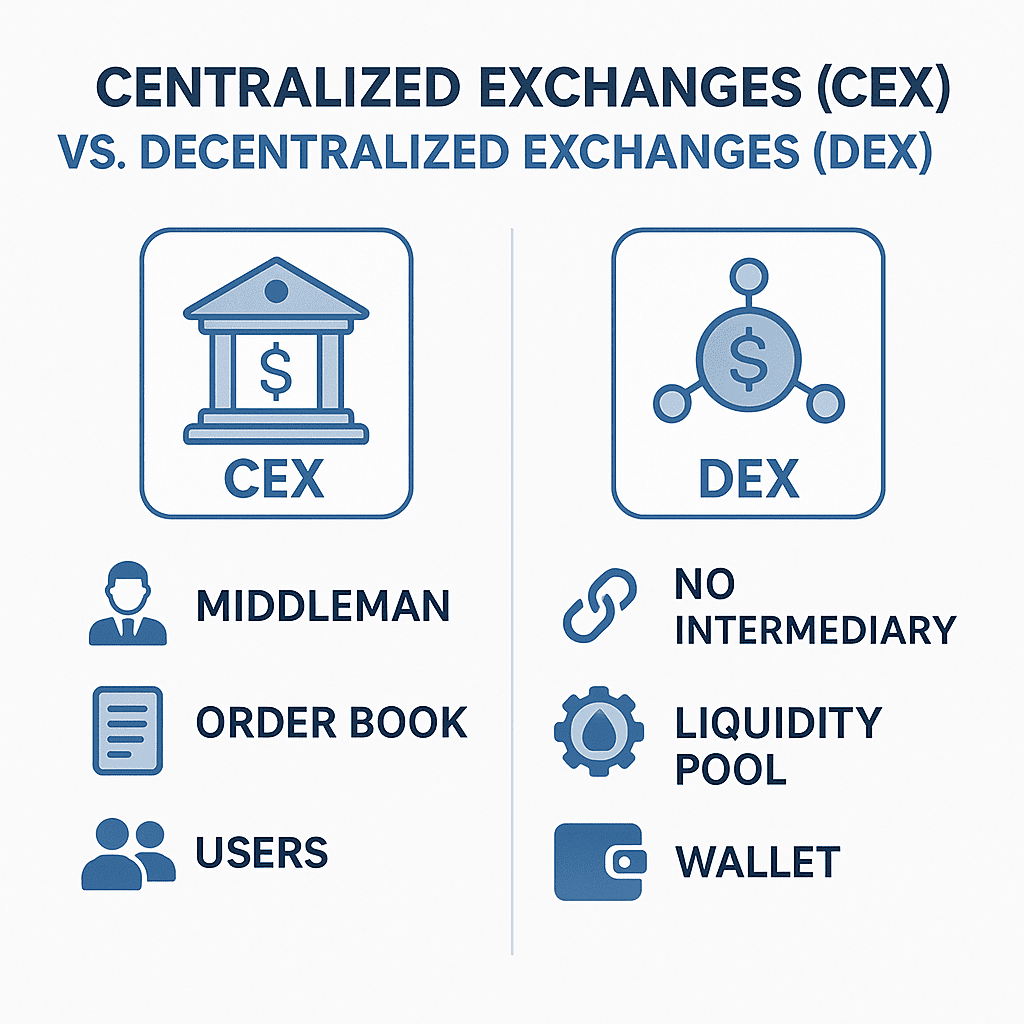
Centralized Exchanges (CEX)
- Role and Operation: A trading platform operated and managed by a centralized company or entity. Users must deposit their digital assets into the exchange’s custodial wallet before buying or selling within the exchange’s internal ledger system. The exchange acts as a matchmaker (similar to a traditional stock exchange’s order book model) and custodian of the assets. Notable CEXs include Binance, Coinbase, and Kraken.
- メリット
- High Liquidity and Trading Depth: Large CEXs typically have a vast user base and trading volume, making it easier to buy and sell mainstream cryptocurrencies quickly at expected prices.
- Rich Trading Features: Offer various trading tools such as spot trading, leveraged trading, futures contracts, options trading, and investment products.
- User-Friendly Experience: Interfaces are usually designed to be intuitive and easy to use, making it suitable for beginners.
- Fiat On-Ramp: Many CEXs support fiat (like USD, EUR) deposits and withdrawals, facilitating user entry and exit.
- カスタマーサポート Typically provide customer support channels to assist users with issues.
- Disadvantages:
- Asset Custody Risks (Counterparty Risk): User assets are held in centralized custody; if the exchange suffers a hacking attack, internal theft, mismanagement, or regulatory shutdown, users may face losses or be unable to withdraw their assets.
- KYC/AML Requirements: Most CEXs require users to complete identity verification to comply with regulations, which may not meet the needs of users seeking anonymity.
- Centralized Operational Risks: The exchange’s operation can be affected by single points of failure, policy changes, or human factors, such as sudden trading halts or decisions on listing/delisting.
- Limited Transparency: The internal matching and clearing processes of the exchange may lack transparency for external users.
Decentralized Exchanges (DEX)
- Principle and Operation: DEXs operate based on blockchain smart contracts, allowing users to trade directly from their non-custodial wallets (like MetaMask) through peer-to-peer (P2P) or peer-to-pool (like AMM models) transactions. Users retain control of their private keys and assets during the trading process without needing to deposit assets into the exchange. Many DEXs use an Automated Market Maker (AMM) model, trading through liquidity pools rather than traditional order books. Notable DEXs include Uniswap, Sushiswap, PancakeSwap, and Curve.
- メリット
- Full Control of Assets: Assets remain in users’ wallets, reducing the risk of loss due to exchange hacks or shutdowns.
- Higher Anonymity: Many DEXs do not require mandatory KYC, allowing for more anonymous trading (while still being aware of the transparency of on-chain transactions).
- Wider Token Selection: DEXs generally have lower entry barriers for new tokens, allowing users to trade a broader variety of emerging tokens or long-tail assets.
- Transparency and Verifiability: The operations of trades and liquidity pools are defined by smart contracts, which are publicly transparent and verifiable on the blockchain.
- Disadvantages:
- Higher User Experience Threshold: Using a DEX typically requires users to have a certain understanding of crypto wallets, Gas fees, and smart contracts, which may not be friendly for beginners.
- Transaction Speed and Costs Dependent on Underlying Blockchain: Transaction confirmation speed and fees (Gas fees) depend on the state of the underlying blockchain network (e.g., high Gas fees during Ethereum network congestion). Layer 2 solutions can help mitigate this issue.
- Fragmented Liquidity: Compared to large CEXs, individual DEXs or specific trading pairs may have poorer liquidity, leading to larger slippage or difficulty executing large orders.
- Smart Contract Vulnerability Risks: If a DEX’s smart contract has vulnerabilities, it may be exploited by attackers to steal funds from liquidity pools.
- Impermanent Loss: In AMM models, liquidity providers may face impermanent loss risks.
- Lack of Fiat On-Ramp: Most DEXs do not directly support fiat trading, requiring users to purchase stablecoins or mainstream cryptocurrencies on CEXs before transferring to DEXs.
How to Choose the Right Trading Platform
When selecting a trading platform, consider the following factors:
- Security: The platform’s historical security record, security measures (like cold wallet storage ratios, insurance funds), and whether it is regulated by authoritative bodies.
- Liquidity and Trading Depth: For frequent or large-scale traders, high liquidity platforms are preferable.
- Trading Fees: Compare transaction fees, deposit/withdrawal fees, and borrowing rates across different platforms.
- Supported Tokens and Trading Pairs: Whether the platform offers the digital assets and trading pairs you are interested in.
- User Experience and Features: Whether the interface is user-friendly, operations are convenient, and required trading tools (like APIs, advanced order types) are provided.
- Customer Service: Whether timely and effective customer support is available.
- Regulatory Compliance and Regional Restrictions: Whether the platform complies with the laws and regulations in your location and whether it serves your region.
- Personal Risk Appetite and Skill Level: If you value asset control and have some technical knowledge, a DEX may be a good choice; if you are a beginner or prefer convenient operations and diverse features, a CEX may be more suitable. Many experienced users combine the use of both CEXs and DEXs.
3.3 Basic Trading Processes and Order Types
Learning Objective: Master the account registration, identity verification, asset deposit/withdrawal, and common order types on centralized trading platforms.
Account Registration and Identity Verification (KYC/KYT Overview)
(Primarily for CEX)
- Registering an Account: Visit the official website of the chosen centralized exchange or download its official app. Typically, registration requires using a valid email address or phone number and setting a sufficiently strong login password. Always enable two-factor authentication (2FA) to enhance account security.
- Identity Verification (KYC – Know Your Customer): To comply with global anti-money laundering (AML) and counter-terrorism financing (CFT) regulations, most CEXs require users to complete identity verification. KYC levels are generally tied to user trading limits, withdrawal limits, and available service features. Common KYC processes include:
- Submitting Basic Personal Information: Name, nationality, date of birth, and residential address.
- Uploading Identification Documents: Typically, valid government-issued documents such as ID cards (front and back), passport personal information page, or driver’s licenses.
- Facial Recognition Verification: Users may be required to take a selfie holding their document or perform liveness checks (e.g., blinking, turning their head as instructed).
- Address Proof: Higher-level verifications may require recent utility bills or bank statements as proof of residence.
- KYT (Know Your Transaction): Exchanges may also monitor users’ trading behavior (KYT) to detect and prevent money laundering, fraud, and other illegal activities. This part is usually performed automatically in the background.
Asset Deposit and Withdrawal
- Deposit: Transfer digital assets from your personal wallet or other platforms to your account on the exchange. Steps include:
- On the exchange’s asset or wallet page, select the cryptocurrency you wish to deposit.
- The exchange will provide a dedicated deposit address and/or MEMO/Tag (some cryptocurrencies require this).
- Critical: Ensure that the chosen deposit network (blockchain, such as ERC-20, TRC-20, BEP-20, Solana, etc.) matches the network you selected when transferring from your external wallet. Choosing the wrong network may result in permanent asset loss.
- Initiate the transfer from your external wallet to the provided deposit address. Wait for the blockchain network to confirm the transaction, and the assets will appear in your exchange account.
- Withdrawal: Transfer digital assets from your exchange account to your personal wallet or another platform. Steps include:
- On the exchange’s asset or wallet page, select the cryptocurrency you wish to withdraw.
- Enter your external receiving wallet address and withdrawal amount. Again, ensure that the withdrawal network matches the network supported by the receiving wallet.
- The exchange typically charges a withdrawal fee.
- After completing security verification (such as email verification code, phone verification code, 2FA code), submit the withdrawal request and wait for the exchange to process and the blockchain to confirm.
Common Order Types
- Market Order: Buy or sell a specified quantity of assets immediately at the best available market price. The advantage is fast execution, almost guaranteeing a trade. The downside is that during rapid market fluctuations or low liquidity, the actual execution price may differ significantly from the price seen when placing the order (known as “slippage”).
- Limit Order: Allows you to set a specific buying price (not exceeding this price) or selling price (not below this price). The order will only be executed when the market price reaches your set limit or better. The advantage is precise control over the execution price. The downside is that if the market price does not reach your limit, the order may remain unexecuted for a long time or never execute.
- Stop-Loss Order: A risk management tool. When the market price reaches your preset stop-loss trigger price, the system will automatically generate a market order (or limit order, known as a stop-limit order) to sell the asset, limiting potential losses.
- Take-Profit Order: Similar to a stop-loss order but used to lock in profits. When the market price reaches your preset take-profit trigger price, the system will automatically generate a market order (or limit order) to sell the asset.
- OCO (One-Cancels-the-Other) Order: Simultaneously places two orders (usually one limit order and the other a stop-loss or stop-limit order). When one of the orders is fully or partially triggered, the other order is automatically canceled. This is commonly used to set profit targets and loss limits simultaneously.
Understanding Trading Interface and Candlestick Chart Basics
- Trading Interface: The trading interface of mainstream exchanges typically includes the following core areas:
- Candlestick Chart Area: Displays the price trend of the selected trading pair over various time intervals (e.g., 1 minute, 5 minutes, 1 hour, daily).
- Order Book: Displays all outstanding buy orders (Bids) and sell orders (Asks) in real-time, along with their corresponding prices and quantities.
- Latest Trade History: Shows a rolling list of completed trades, including prices and quantities.
- Order Entry Panel: Users select order types (market, limit, etc.), input prices (for limit orders), quantities, and execute buy or sell operations.
- Asset Balances and Position Information: Displays the available balances and holdings of relevant cryptocurrencies in the user’s account.
- Candlestick Chart Basics: Candlestick charts are among the most critical tools in technical analysis. Each candlestick represents price fluctuations over a specific time period and includes four key price points:
- Open: The price at the beginning of the period.
- Close: The price at the end of the period.
- High: The highest price reached during the period.
- Low: The lowest price reached during the period.
The “body” of the candlestick is formed by the open and close prices. If the close price is higher than the open price (indicating a rise), the body is typically displayed in green or white (bullish candle); if the close price is lower than the open price (indicating a decline), the body is usually shown in red or black (bearish candle). The lines above and below the body are called “shadows,” with the upper shadow representing the high and the lower shadow representing the low. Different candlestick patterns can reflect the market’s bullish or bearish sentiment and potential trend changes.
3.4 Risk Management in Digital Asset Trading
Learning Objective: Establish a solid risk awareness, identify major risk types in digital asset trading, and learn basic yet essential risk control strategies and capital management principles.
Market Volatility Risk
The digital asset market is known for its extreme price volatility, with prices potentially experiencing rapid increases or decreases in a short period. This means investors may face significant potential gains but also substantial potential loss risks. It is crucial to recognize this volatility and only invest funds that can be afforded to lose.
Platform Security Risks
- Centralized Exchanges (CEX): They may be targets for hacking attacks, internal theft, technical failures, operational shutdowns, or sudden regulatory crackdowns, leading to potential losses or inability to withdraw funds stored on the exchange.
- Decentralized Exchanges (DEX): Their core relies on smart contracts, which may have vulnerabilities that could be exploited by attackers, resulting in funds being stolen from liquidity pools.
Liquidity Risk
Certain low-market-cap coins, newly issued tokens, or assets traded on small exchanges may face liquidity issues. This means it may be difficult to buy or sell sufficient quantities of assets quickly at expected prices when needed, or large trades may significantly impact market prices (high slippage).
Operational Risks
These include user errors (e.g., entering incorrect addresses, selecting the wrong network, exposing private keys), phishing scams, and malware attacks.
Emotional Trading Risks (FOMO/FUD)
- FOMO (Fear Of Missing Out): When the market rises quickly, investors may buy in blindly out of fear of missing out, often purchasing at temporary peaks.
- FUD (Fear, Uncertainty, Doubt): During negative news or price declines, investors may panic and sell assets, potentially at unnecessary low points.
Decisions should be based on rational analysis and established trading plans rather than short-term market emotions.
Establishing a Trading Plan and Capital Management Principles
This is the cornerstone of risk management.
- DYOR (Do Your Own Research): Before investing in any digital asset, conduct thorough, independent research. Understand the project’s fundamentals (white paper, team background, technical architecture, tokenomics), market prospects, community activity, and competitive landscape. Avoid blindly trusting recommendations or so-called “insider information.”
- Set Clear Stop-Loss and Take-Profit Points: Before executing each trade, determine reasonable stop-loss and profit target prices based on your risk tolerance and market analysis, and adhere strictly to these limits. This helps control the maximum loss of individual trades and locks in profits when expected gains are reached.
- 多角化: “Don’t put all your eggs in one basket.” Allocate funds across different types, sectors, and less correlated digital assets or investment strategies to reduce overall portfolio risk. However, avoid over-diversification, which can make management difficult and dilute potential returns.
- ポジションサイジング: Control the amount invested in each trade as a proportion of your total investable funds. For example, set the maximum loss per trade to not exceed 1%-2% of total capital. This helps prevent significant losses from impacting overall trading psychology and account health.
- Avoid Excessive Leverage: While leverage trading can amplify profits, it also magnifies losses, potentially leading to liquidation. Beginners should be extremely cautious when using leverage or avoid it entirely. Even experienced traders should strictly control leverage ratios and positions.
- Regular evaluation and adjustment of strategies: Market conditions are constantly changing, you should review your trading performance on a regular basis, sum up your experience and lessons learnt, and make timely adjustments to your trading strategies and risk management plans according to the market environment and your own situation.
3.5 Asset Security Practices in Trading
Learning Objective: Master specific operational methods and core principles for protecting personal asset security during all stages of digital asset trading.
Tiered Storage and “Cold-Hot Separation” Strategy
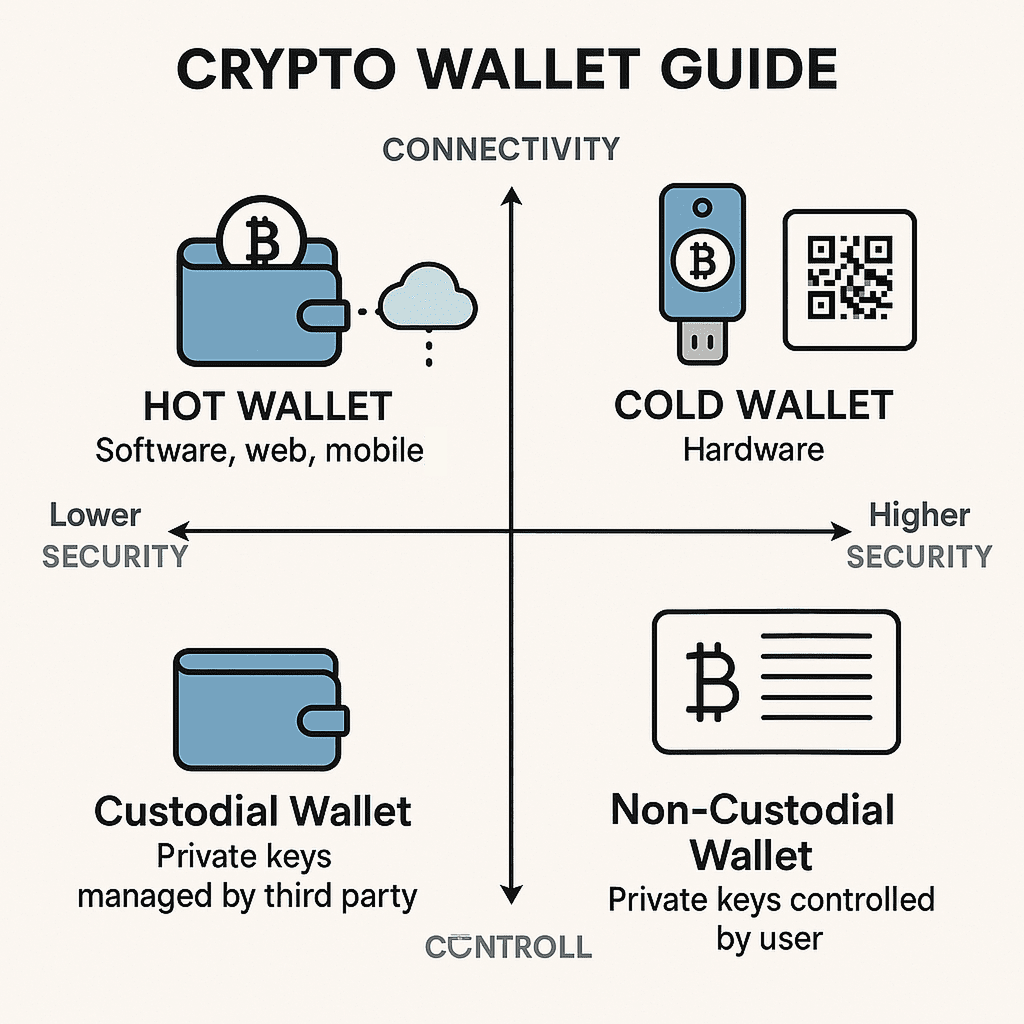
This is the core principle for protecting large assets.
- Cold Wallet (Primarily Hardware Wallets): Used to store the majority (e.g., 80%-90%) of digital assets that are not frequently traded and are intended for long-term holding. Private keys in cold wallets are stored offline, maximizing protection against online hacking attacks.
- Hot Wallet (Software Wallets/Exchange Accounts): Used to store a small amount (e.g., 10%-20%) of assets that are expected to be used for trading, payments, or interacting with DApps in the near term. While convenient, they carry higher risks due to their online nature.
Regularly transfer accumulated larger amounts of assets from the hot wallet to the cold wallet for secure storage.
Strengthening Trading Platform Account Security
- Set Unique and Strong Login Passwords: Create complex passwords for each exchange account that differ from those used on other websites, incorporating uppercase and lowercase letters, numbers, and special characters. Regularly change these passwords and consider using a password manager to generate and store them.
- Enable Two-Factor Authentication (2FA): All accounts on exchanges that support 2FA must have it enabled. Prioritize time-based one-time password (TOTP) applications (like Google Authenticator or Authy), which are more secure than SMS verification codes (SMS 2FA can be vulnerable to SIM swap attacks). If possible, consider using hardware security keys (like YubiKey) for 2FA.
- Whitelist Withdrawal Addresses: If the exchange provides this feature, be sure to enable it. Add commonly used, verified personal wallet addresses to the whitelist. This way, even if the account is compromised, attackers can only withdraw assets to these pre-set addresses, increasing the difficulty of theft.
- API Key Security Management: If you need to create API keys for trading bots or connecting to third-party services, adhere to the principle of least privilege, granting only necessary permissions (for example, if only data reading is needed, do not grant trading or withdrawal permissions). Set IP whitelisting for API keys and rotate them regularly. Safeguard the API Secret Key and avoid exposing it.
- Device Binding and Login Monitoring: Some exchanges offer features for binding commonly used devices and checking login history. Regularly review for any unusual login activities.
Preventing Phishing and Social Engineering Attacks
- Verify Official URLs: Before logging into exchange or wallet websites, ensure the URL in the browser address bar is the correct official domain, being cautious of similarly spelled phishing sites. It is best to bookmark frequently used official URLs.
- Do Not Trust Unknown Emails, Messages, or Social Media Posts: Officials will never ask for your account password, 2FA codes, private keys, or mnemonic phrases through these channels, nor will they request you to click links for “account upgrades” or transfer funds to a “secure address.”
- Beware of Fake Apps or Browser Extensions: Only download exchange apps or wallet software from official websites or trusted app stores.
- Regularly Check Account Activity and Authorizations: Periodically log in to check transaction records, login history, and authorizations for your exchange account and on-chain wallet addresses. Promptly revoke any DApp authorizations that are no longer needed or appear suspicious.
Using Secure Network Environments and Devices
- Avoid conducting trading operations or logging into sensitive accounts on public computers or insecure public Wi-Fi networks.
- Ensure that the personal computer and mobile device used for trading have the latest versions of operating systems, browsers, and antivirus software, and are free from malware infections.
Case Warning: The Importance of Personal Asset Information Security
As highlighted by the South African kidnapping case involving cryptocurrency holders in 2024, such malicious incidents underscore the importance of protecting personal information and asset holdings in the digital asset space. Avoid flaunting wealth in public or overly exposing information about substantial holdings of cryptocurrencies, as this can reduce the risk of becoming a target for real-life crimes. Adopting a multi-layered and comprehensive security awareness and measures is essential.
3.6 Basics of Digital Asset Valuation and Compliance Requirements
Learning Objective: Gain a preliminary framework for common valuation methods of digital assets and understand basic tax compliance concepts, particularly using the IRS regulations in the United States as an example.
Introduction to Digital Asset Valuation Basics
Valuing digital assets is a complex and still-developing field, with no unified and widely accepted standard model. Common analytical frameworks and considerations include:
- Fundamental Analysis: Similar to traditional stock analysis, it aims to assess the intrinsic value of a digital asset (or its underlying project/protocol). Considerations typically include:
- Project Whitepaper and Technical Architecture: The project’s vision, the problems it addresses, and the innovation, feasibility, and security of its technical solutions.
- Team Background and Execution Capability: The experience, expertise, industry reputation of core team members, and the project’s development progress and roadmap realization.
- トークノミクス The total supply of tokens, distribution mechanisms (proportions for the team, investors, community), release schedules, core uses (payment, governance, staking), burn mechanisms, and the sustainability of incentive models.
- Market Demand and Use Cases: The target market size, the actual pain points addressed, potential for user adoption, and network effects.
- Community Activity and User Base: The size and engagement of the community, developer activity, number of active addresses on-chain, transaction volumes, etc.
- Competitive Landscape and Partnerships: The project’s competitive position in its sector, differentiation advantages, and cooperative relationships with other projects or institutions.
- On-Chain Data Analysis: Analyzing data provided by blockchain explorers, such as transaction volume, token holder distribution, large transfers, and smart contract interaction data, to assess network health and market sentiment.
- Technical Analysis: Studying historical price charts, trading volume data, and various technical indicators to identify market trends, support/resistance levels, and buy/sell signals to predict future price movements. Common tools include candlestick patterns, trend lines, moving averages, relative strength index (RSI), and MACD. Technical analysis focuses more on market psychology and price behavior rather than the intrinsic value of the project itself.
- Relative Valuation Method: Comparing the target asset to similar comparable assets (or projects) in the market based on key indicators (such as market cap/user numbers, market cap/trading volume, price-to-sales ratios) to determine whether its valuation is reasonable.
- Professional Institutions’ Valuation Models: Some professional digital asset research institutions and funds (like HashKey Capital) develop more complex, multi-dimensional valuation models that may combine macroeconomic factors, industry development prospects, technological innovation cycles, regulatory environments, and employ differentiated valuation frameworks for different types of digital assets (like L1 coins, DeFi protocol tokens, NFTs, etc.). However, these models are usually not publicly disclosed.
Compliance Requirements (Brief Overview Using U.S. IRS Tax Treatment as an Example)
Tax Treatment of Digital Assets
In the U.S., the Internal Revenue Service (IRS) generally classifies cryptocurrencies and digital assets as “property” rather than “currency” for tax purposes. This means that nearly all transactions involving digital assets may result in taxable events.
Common Taxable Events:
- Selling Digital Assets for Fiat: For example, selling Bitcoin for USD.
- Exchanging One Digital Asset for Another: For example, using Bitcoin to buy Ethereum.
- Using Digital Assets to Purchase Goods or Services: For example, purchasing coffee with Bitcoin.
- Receiving Digital Assets as Compensation: For example, digital assets obtained through mining, staking, airdrops, or work compensation are typically viewed as income and taxed based on their fair market value at the time of receipt.
Capital Gains and Losses:
When selling or exchanging held digital assets, if the selling price (or fair market value at the time of exchange) exceeds your cost basis (usually the price you paid for the asset plus related transaction fees), capital gains are realized and subject to tax. Conversely, if the selling price is lower than the cost basis, capital losses occur, which can offset other capital gains and potentially ordinary income within certain limits. The duration of asset holding (typically one year) affects the capital gains tax rate (short-term capital gains rates are usually higher than long-term rates).
Record-Keeping Obligations:
Taxpayers are responsible for accurately and thoroughly recording all digital asset transactions, including transaction dates, types and quantities of assets bought/sold (or exchanged), prices (in fiat), transaction fees, and counterparty addresses (in certain cases). These records form the basis for tax calculations and potential audits.
Reporting Requirements and Regulatory Trends:
U.S. taxpayers must report their digital asset trading activities and related income/gains on their annual tax returns. The IRS has increasingly strengthened its regulatory and enforcement efforts regarding digital asset trading. For instance, starting in 2025, the U.S. will require cryptocurrency exchanges and brokers to provide 1099-series tax forms (like 1099-DA) to the IRS and users, detailing clients’ digital asset trading information, which will significantly enhance the transparency of tax compliance.
Important Note:
Tax law is extremely complex, varies by country/region, and is continually evolving. The above introduction to U.S. tax treatment is general information and does not constitute tax advice. For specific digital asset tax issues, consult a professional tax advisor or accountant in your jurisdiction.
3.7 Recent Trends and Security Cases in Digital Asset Trading
Learning Objective: Understand the main types of security threats currently facing the digital asset trading market, recognize the evolution of the regulatory environment and its potential impact on the market, and focus on advancements in trading platform security technologies.
Overview of Global Trading Security Risks
Digital asset traders face a variety of security threats and must remain vigilant:
- Phishing: Remains one of the most common and harmful attack methods in the digital asset space. Attackers create fake exchange login pages, impersonate official emails, use malicious apps/browser extensions, or set up fake customer service accounts on social media to trick users into entering login credentials (username, password), 2FA codes, private keys, or mnemonic phrases, or authorize malicious smart contracts.
- Malware and Viruses: Trojans, keyloggers, clipboard hijackers, and other malicious software may lurk on users’ computers or mobile devices, stealing sensitive information (such as wallet passwords, private keys) or replacing copied wallet addresses with those of attackers.
- SIM Card Swap Attacks: Attackers deceive or collude with telecom operators to transfer the victim’s phone number to a SIM card under their control. Once successful, attackers can receive the victim’s SMS verification codes, bypassing SMS-based two-factor authentication (SMS 2FA) to take control of their exchange accounts or other services linked to the phone number.
- Exchange Security Vulnerabilities and Theft Incidents: Despite significant investments in security by large exchanges, they cannot completely eliminate the risk of attacks by highly skilled hacker organizations. Historical incidents of hacking of exchange hot wallets and user data breaches have led to significant asset losses for users.
- DEX Smart Contract Risks: The core of decentralized exchanges is smart contracts. If the code of a DEX’s smart contract contains vulnerabilities or logical flaws, attackers may exploit them to steal funds from users’ liquidity pools or engage in price manipulation.
- Physical Security Threats and Violent Crimes: As highlighted by the South African case, individuals who publicly flaunt large holdings of cryptocurrencies or whose sensitive information (such as home addresses or asset situations) is leaked may become targets for kidnapping or robbery. This risk is especially pronounced in regions with poor security or weak regulation and enforcement of crypto assets.
- Rug Pull: In emerging, poorly regulated projects (especially small tokens or NFT projects on some DEXs), project teams may abruptly withdraw liquidity and abandon projects after raising funds or inflating token prices, rendering investors’ NFTs worthless.
Evolution and Impact of the Regulatory Environment
- Increasingly Strict and Clear Global Regulatory Trends: Governments and international regulatory bodies (like FATF, IOSCO, and FSB) are gradually strengthening oversight of the digital asset market to protect investors, prevent money laundering, and maintain financial market stability. Although progress and focus vary by country, the overall trend is shifting from “hands-off observation” to “active regulation.”
- Strengthening KYC/AML/CFT Requirements: KYC (Know Your Customer), AML (Anti-Money Laundering), and CFT (Counter-Terrorism Financing) requirements for cryptocurrency exchanges, wallet service providers, and other Virtual Asset Service Providers (VASPs) are becoming increasingly stringent, aligning more closely with traditional financial institutions. FATF’s “Travel Rule” requires VASPs to exchange information about the parties involved in transfers, which is being gradually legislated in various countries.
- Tax Compliance and Information Reporting: Tax authorities globally are increasingly focusing on taxing digital asset transactions and enhancing information collection and reporting requirements. For example, the upcoming implementation of the 1099-DA form in the U.S.
- Specialized Regulation for Stablecoins: Many countries are drafting or implementing specific regulatory frameworks targeting stablecoins, addressing aspects such as reserve transparency, issuance qualifications, and operational risks (e.g., the EU’s MiCA regulation).
- Clarification of Regulatory Oversight for Security Tokens: Clarifying which digital assets are classified as securities and bringing them under existing securities regulations.
インパクト
Stricter and clearer regulations will aid in the long-term healthy development of the market, enhance institutional investor confidence, and reduce market manipulation and fraud. However, it may also increase compliance costs for VASPs, limit certain business models that emphasize anonymity, and potentially impact the pace of market innovation.
Advancements in Platform Security Technologies
To address increasingly complex security threats and regulatory requirements, trading platforms are continually upgrading their security technologies:
- Enhanced AML/KYT Systems: Exchanges are adopting advanced technologies (such as AI, machine learning, big data analysis, and blockchain analysis tools) to monitor and identify suspicious trading patterns and high-risk address affiliations in real-time, fulfilling anti-money laundering and risk control obligations.
- Multi-layered Security Framework: This includes cold wallet storage for the majority of assets, multi-signature authorization for hot wallets, hardware security modules (HSM) protecting private keys, anomaly detection and real-time alert systems, withdrawal delays with manual review mechanisms, and establishing user asset protection funds (like Binance’s SAFU fund).
- Smart Risk Control Systems: These evaluate account risk in real-time based on user behavior analysis, device fingerprints, IP address monitoring, and other multi-dimensional information to identify potential account theft or fraudulent behavior.
- Security Audits and Bug Bounty Programs: Regularly inviting reputable third-party cybersecurity firms to conduct comprehensive security audits and penetration tests on platform systems. Additionally, establishing bug bounty programs to encourage white-hat hackers and security researchers to report potential security issues.
- User Security Education and Tools: Providing comprehensive user security guidelines, promoting the use of strong 2FA methods, and offering phishing email detection tools.
In summary, awareness of security threats and proactive measures are critical in the digital asset trading environment, ensuring not only the protection of personal assets but also fostering a more secure trading ecosystem.

