2.1 Basics of Cryptocurrency Wallets
學習目標: Understand the core functions of cryptocurrency wallets and master key concepts such as public keys, private keys, wallet addresses, and mnemonic phrases, along with their interrelations.
Functions and Role of Wallets
Cryptocurrency wallets are essential tools for managing and using cryptocurrencies and other digital assets. Unlike traditional wallets, they do not “store” your assets in a physical sense (as digital assets are recorded on the blockchain); instead, they securely store the cryptographic information necessary to access and control these on-chain assets—namely, the private key. Key functions include:
- Generating and managing key pairs
- Receiving and sending digital assets
- Checking balances and transaction history
- Interacting with decentralized applications (DApps)
Public Key, Private Key, and Wallet Address
These are the core components of asymmetric encryption and the foundation of cryptocurrency wallet operations.
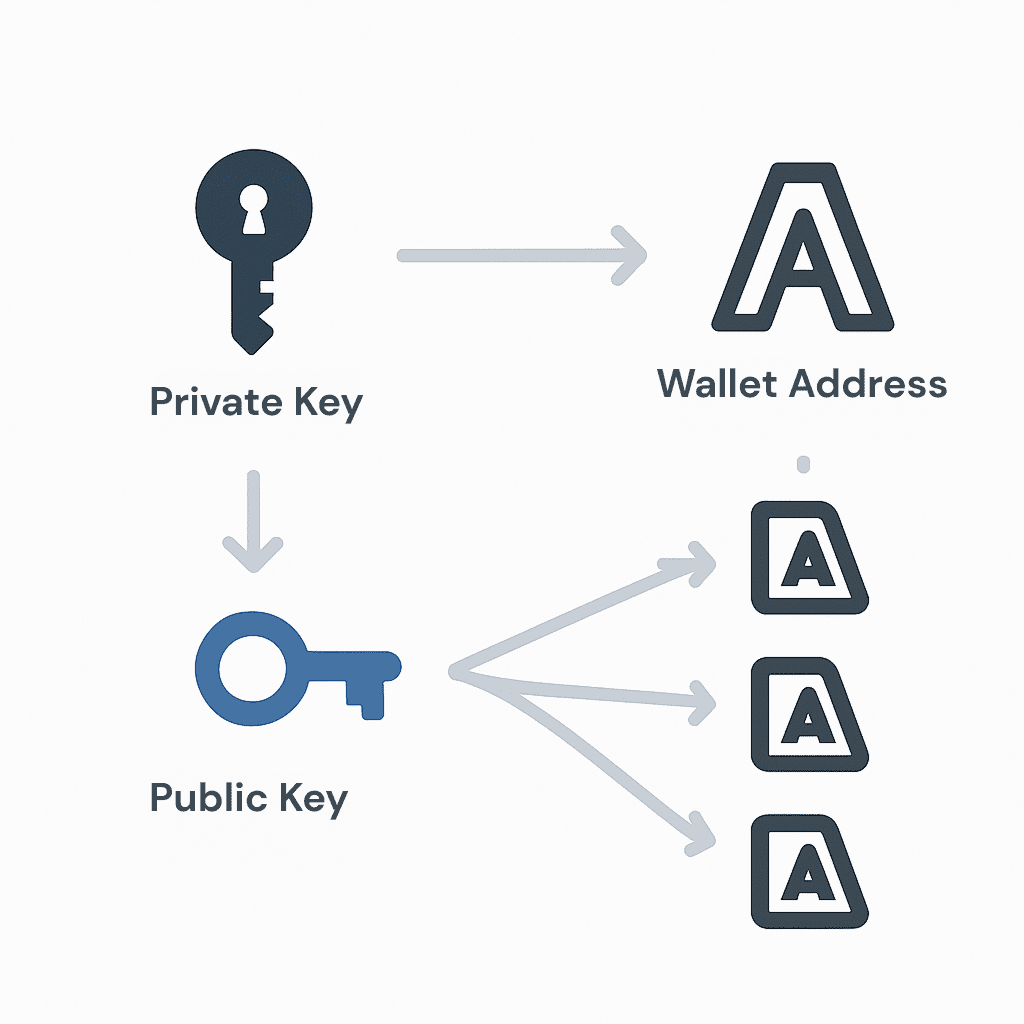
- 私密金鑰: A long string of randomly generated, highly confidential alphanumeric characters. It is the sole credential granting complete control over the assets in your wallet, akin to a safe’s key. Anyone with the private key can access the corresponding address’s assets; hence, it must never be shared and must be securely backed up. It is required to sign transactions (i.e., authorize asset transfers).
- 公開金鑰: Generated from the private key via a one-way cryptographic algorithm. The public key can be safely shared with others to receive digital assets, similar to a bank account number. Although the public key is public, it cannot be reverse-engineered to deduce the private key, ensuring security.
- 錢包地址: Typically a shorter, user-friendly string generated from the public key through further hashing and encoding (e.g., Base58Check encoding). It is the “receiving address” you provide to others for transfers. One private key can derive one public key, and one public key can derive one or more wallet addresses in different formats.
- Mnemonic Phrase (Seed Phrase): Usually a sequence of 12, 18, or 24 common words arranged in a specific order. This phrase is generated from a high-entropy random number (the seed for the private key) using standardized algorithms (like BIP-39), making it easier for humans to write down and back up private keys. The mnemonic phrase can restore and derive all private keys, public keys, and addresses in the wallet. Therefore, its importance is equivalent to that of the private key and must be backed up securely (e.g., handwritten on paper and stored in multiple secure locations) to prevent exposure.
2.2 Types of Cryptocurrency Wallets
學習目標: Clearly distinguish between custodial and non-custodial wallets and understand the differences in security and convenience between hot wallets and cold wallets, along with their applicable scenarios.
Types of Cryptocurrency Wallets
| Wallets | Custodial Wallets | Non-Custodial Wallets |
| 定義 | Managed by third-party service providers (e.g., cryptocurrency exchanges, some online wallet services) that hold and manage users’ private keys. Users typically log in via an account password to access their assets | Users fully control their private keys and mnemonic phrases. Wallet software merely serves as a tool for managing and using these keys. |
| 優勢 | Relatively easy to use, akin to traditional online banking. If users forget their login password, they can often recover their account access through customer support. | Users have absolute control and ownership over their assets without relying on third parties, aligning with the decentralized and autonomous spirit of blockchain |
| 缺點 | Users do not truly control their private keys, meaning they do not have complete control over their assets. “Not your keys, not your coins.” The security of assets relies on the custodian’s security measures and reputation. If the custodian is hacked, goes bankrupt, or faces regulatory freezes, users’ assets may be at risk. | Users bear full responsibility for securing their private keys and mnemonic phrases. If lost or exposed, assets may be permanently unrecoverable, and no customer support is available. Higher security awareness and operational skills are required |
Hot Wallet vs. Cold Wallet
| Type | Description |
|---|---|
| Hot Wallet | Private keys are stored on devices that are always or frequently connected to the internet. Typically in software form, such as desktop applications (Desktop Wallets), mobile app wallets (Mobile Wallets), or browser extension wallets (Browser Extension Wallets). |
| 優勢 | Convenient and fast, suitable for frequent trading or interaction with DApps. |
| 缺點 | Due to constant internet connectivity, private keys are exposed to online threats (e.g., malware, phishing sites, remote hacking). |
| Cold Wallet | Private keys are generated and stored completely offline or seldom connect to the internet. The main goal is to isolate private keys to minimize online risks. |
| 硬體錢包 | The most common type of cold wallet. It is a dedicated physical device (like a USB drive) where private keys are generated and stored in a secure chip within the device. Transactions are signed inside the device; private keys never leave it (e.g., Ledger, Trezor). |
| Paper Wallet | Prints private keys and corresponding addresses in QR code or text form. Completely offline but must be protected from physical damage (fire, water) and loss risks. |
| Other Cold Storage Methods | Such as backing up private keys on offline computers or USB drives. |
| 優勢 | Extremely high security, effectively guarding against various online threats. Suitable for long-term storage of significant digital assets. |
| 缺點 | Relatively inconvenient to operate, not suitable for high-frequency trading. Hardware wallets incur purchase costs. |
Multi-Signature (Multi-Sig) Wallets
These wallets require a specified number of signatures (e.g., a configuration of “2 of 3” where at least two of three private keys must jointly sign to authorize a transaction). This greatly enhances security, as even if one private key is exposed or one authorizing individual makes a mistake, the assets remain secure. Multi-sig wallets are particularly suitable for corporate fund management, jointly managed assets, or as a means to enhance individual security.
2.3 Security and Risks of Cryptocurrency Wallets
學習目標: Identify the main risks associated with using cryptocurrency wallets and understand the corresponding prevention principles.
風險
- Irreversibility of Transactions: Once confirmed and recorded on the blockchain, transactions are typically irreversible or unchangeable. If users mistakenly send assets to the wrong address or are tricked into transferring funds in a scam, these assets may be permanently lost and difficult to recover.
- Private Key/Mnemonic Phrase Leakage and Hacking Risks: The private key and mnemonic phrase are the only credentials controlling wallet assets. If exposed to unauthorized third parties (e.g., via malware, keyloggers, phishing sites, insecure network environments, social engineering attacks), attackers can fully control and steal all assets in the wallet. Hot wallets, due to their online nature, are at higher risk in this regard.
- Phishing and Social Engineering Risks: Attackers may use counterfeit official websites, impersonated customer service emails or messages, malicious apps, or browser extensions to trick users into entering their private keys, mnemonic phrases, login passwords, or authorizing malicious smart contracts, thus stealing assets.
- Vulnerabilities in Wallet Applications: Both software wallets and hardware wallets’ firmware may have undiscovered security vulnerabilities that can be exploited by technically skilled attackers. Therefore, choosing reputable, well-audited, and regularly updated wallet products is crucial.
- Physical Security Risks: For hardware wallets, the loss, damage, or theft of the device itself poses risks. For paper wallets or handwritten mnemonic phrase backups, considerations include protection against fire, water, theft, and fading.
- Custodial Risk (for Custodial Wallets): When using custodial wallets (like exchange accounts), the security of users’ assets entirely depends on the custodian’s security measures and operational reputation. Historical incidents of exchanges being hacked and resulting in user asset losses, or users being unable to withdraw due to the exchange’s mismanagement or regulatory issues, have occurred.
- Operational Mistake Risks: User errors, such as copying incorrect receiving addresses, entering wrong transfer amounts, or operating wallets on insecure devices, can lead to asset losses.
- Malware and Virus Risks: Computers or mobile devices infected with viruses or trojans may lead to the theft of private keys or hijacking of transactions.
2.4 Best Practices for Wallet Security
學習目標: Systematically learn specific, actionable steps and strategies to protect mnemonic phrases, private keys, and wallet applications.
Best Practices
- Extreme Protection of Mnemonic Phrases/Private Keys: This is paramount for wallet security.
- Secure Generation and Recording: Ensure to generate mnemonic phrases in a secure, offline environment. Write them down accurately and preferably in multiple copies.
- Offline Physical Storage: Backup handwritten mnemonic phrases in extremely secure, concealed, and physically protected locations (e.g., fireproof and waterproof safes, bank vaults). Consider distributed storage to reduce single-point failure risks.
- Prohibit Digital Storage: Absolutely avoid storing mnemonic phrases in any digital form (e.g., screenshots, photos, text files, emails, cloud storage, chat logs) on internet-connected devices. These methods are highly susceptible to hacker theft.
- Never Share with Anyone: Never disclose your complete mnemonic phrase or private key to anyone (including self-proclaimed official customer service representatives, friends, or family). Anyone asking for this information is a scammer.
- Enhance Physical Protection: Consider using more durable backup methods, such as metal mnemonic phrase plates (fireproof, waterproof, corrosion-resistant) for engraving mnemonic phrases.
- Use Strong Passwords and Enable Two-Factor Authentication (2FA):
- Set complex, unique, and hard-to-guess login passwords or PINs for wallet applications (especially software wallets).
- If the wallet or related services (e.g., exchanges) support it, always enable two-factor authentication (2FA) using OTP apps like Google Authenticator, Authy, or hardware security keys like YubiKey. Avoid using less secure SMS verification codes.
- Utilize Operating System Security Features: Some mobile wallets (e.g., KryptoGO Wallet) leverage operating system-provided secure areas (like iOS’s Secure Enclave/Keychain, Android’s Keystore/TEE) to encrypt and store encrypted versions of mnemonic phrases or private keys, providing additional hardware-level security protection against malware.
- Choose Reputable and Audited Wallets: Prioritize well-known, widely used wallets with good security records, preferably open-source or independently audited by third parties. Check user reviews and professional assessments.
- Keep Software and Systems Updated: Regularly update your wallet software, operating systems, browsers, and antivirus software to the latest versions to patch known security vulnerabilities.
- Be Vigilant Against Phishing Attacks and Malicious Links:
- Carefully verify website domain names, email sender addresses, and app sources. Never trust unknown links, attachments, or app download requests.
- Official teams will never proactively ask for your private keys, mnemonic phrases, or request you to transfer funds to a specific address through unofficial channels.
- Use Dedicated and Clean Devices: If possible, consider using a dedicated computer or mobile device solely for cryptocurrency operations, maintaining a clean system to reduce the risk of malware infection.
- Conduct Small Tests and Cautious Authorizations: Before conducting large transactions or interacting with new DApps (especially those involving smart contract authorizations), first conduct small transactions for testing and carefully review requested permissions. Regularly check and revoke unnecessary DApp authorizations.
- Regularly Check and Backup Validity: Periodically verify that your backups are intact, clearly legible, and functional. Occasionally conduct a small recovery test to ensure backup effectiveness.
2.5 Advanced Wallet Security Issues
學習目標: Gain a deeper understanding of the operational principles of multi-signature wallets and their applicable scenarios, recognize the importance of maintaining device security, and consider the security practices of wallet providers.
多重簽名錢包
Operation and Applicable Scenarios:
- Principle: Multi-signature wallets require a specified number of authorized keys (M private keys) with at least N (N ≤ M, e.g., common configurations like “2 of 3” or “3 of 5”) to jointly sign to execute a transaction or operation. This means that the leakage, loss, or error (or malicious behavior) of a single private key will not lead to asset loss, as additional signatures are needed to complete a transaction. It enhances security by decentralizing control.
- Applicable Scenarios:
- Corporate Fund Management: Prevents internal malfeasance or operational mistakes, ensuring the security of large corporate assets requiring approval from multiple department heads or designated personnel.
- Joint Accounts: Suitable for family members, business partners, or project teams jointly managing assets, where any operation requires multiple parties’ consent.
- Enhanced Personal Security: Individual users can store different private keys in separate secure devices or locations (e.g., one in a hardware wallet, one on a secure computer, one held by a trusted person). Even if one is compromised, the assets remain secure.
- Custodial and Arbitration Services: In transactions requiring third-party trust, multi-sig can establish arbitration mechanisms, where one signature is held by each of the buying and selling parties and one by the arbitrator.
- DAO Treasury Management: Decentralized Autonomous Organizations (DAOs) often use multi-signature wallets to manage community funds, ensuring that fund usage aligns with community resolutions.
Device Security Checks
Antivirus, Firewalls, Root/Jailbreak Risks:
- Antivirus Software and Firewalls: Ensure your devices have the latest versions of reputable antivirus software and firewalls installed, keeping the definitions up to date and regularly conducting full scans.
- Avoid Rooted or Jailbroken Devices: Rooting (Android) or jailbreaking (iOS) bypasses the operating system’s built-in security restrictions and sandbox mechanisms, making devices more susceptible to malware attacks and privilege escalation, significantly increasing the risk of private key theft. It is strongly recommended to avoid using cryptocurrency wallets on rooted or jailbroken devices, especially those storing significant assets.
- Operating System and Application Updates: Timely install security updates and patches for the operating system and all applications (especially wallet apps and browsers).
- Cautious Authorization of Application Permissions: Carefully review the permissions requested by applications, particularly regarding storage access, network connectivity, camera, microphone, and location information. Grant only the minimum necessary permissions.
- Be Cautious with Public Wi-Fi: Avoid conducting sensitive wallet operations or entering passwords on insecure public Wi-Fi networks, as these networks may be monitored or subject to man-in-the-middle attacks. If necessary, use a VPN.
Code Review, Penetration Testing, and Security Certification
Industry Practices (e.g., KryptoGO):
Reputable wallet providers invest significant resources to ensure product security. Common security practices in the industry include:
- Code Audits: Comprehensive reviews of the wallet’s source code by internal security teams and/or independent third-party security firms to identify potential vulnerabilities and logical flaws.
- Penetration Testing: Simulating hacker attacks to test the wallet system’s defense capabilities from external (black-box testing) or internal (gray-box/white-box testing) perspectives.
- Secure Software Development Lifecycle (SSDLC): Incorporating security considerations and practices at every stage of software development (design, coding, testing, deployment, maintenance).
- Security Certifications and Compliance: Obtaining international standard certifications such as ISO 27001 (Information Security Management System) and ISO 27701 (Privacy Information Management System) demonstrates recognized levels of information security and privacy protection. Certifications mentioned for KryptoGO are critical references for assessing wallet providers’ security commitments.
- Bug Bounty Programs: Encouraging security researchers and white-hat hackers to discover and report product vulnerabilities, providing rewards for successful findings.
- Protecting Development Environments: Strict security measures are necessary for developers’ devices and work environments to guard against supply chain attacks or social engineering attacks.
Considerations for Open Source Wallets
- 優勢: Open code transparency allows developers and security experts worldwide to collaboratively review and helps identify and fix potential vulnerabilities more quickly, theoretically enhancing user trust and fostering community participation and innovation.
- 缺點: Attackers can also study open-source code to find exploitable vulnerabilities. Therefore, being open-source does not directly equate to security; it relies on a strong development team for maintenance, active community oversight, and regular professional security audits. Some wallets may choose not to fully open-source their core security modules to complicate attackers’ analysis but will compensate for reduced transparency with more frequent third-party audits and penetration testing.

