7.1 Definition and Importance of KYC
학습 목표: Define KYC and understand its core position in financial compliance.
What is KYC?
KYC, or “Know Your Customer,” is a regulatory requirement and business practice that mandates financial institutions (such as banks, securities firms, payment institutions) and an increasing number of non-financial sectors (like cryptocurrency exchanges, real estate agents) to identify and verify the identity of customers before establishing a business relationship and throughout its duration, as well as to understand their business activities and risk profiles.
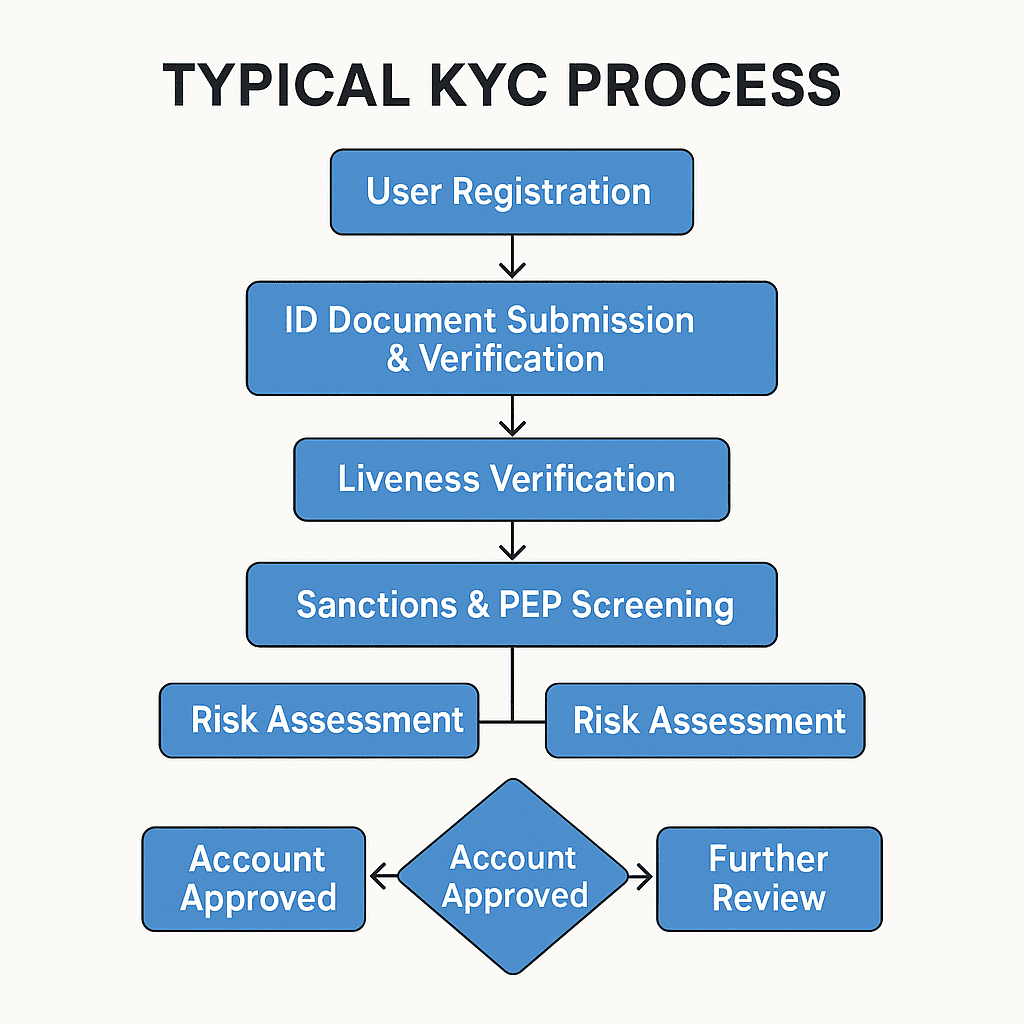
Objectives of KYC:
- Identity Verification: Confirming that customers are who they claim to be.
- Risk Assessment: Evaluating the financial crime risks that customers may pose, such as money laundering, terrorist financing, and fraud.
- Compliance Adherence: Meeting relevant legal and regulatory requirements to avoid regulatory penalties and reputational damage.
Role of KYC in Preventing Financial Crimes:
KYC is a cornerstone of the Anti-Money Laundering (AML) and Combating the Financing of Terrorism (CFT) frameworks. By understanding customers’ true identities and sources of funds, financial institutions can more effectively identify and report suspicious activities, preventing illegal funds from entering the financial system and maintaining the stability and integrity of financial markets.
7.2 Core Components of KYC
학습 목표: Understand the key steps involved in a complete KYC process.
A complete KYC process typically includes the following core components:
Customer Identification Program (CIP):
- Collecting basic identity information from customers, such as name, date of birth, address, and identification number (for individual customers); or company name, registration number, registered address, and beneficial ownership information (for corporate customers).
- Verifying the authenticity of the provided information, usually by cross-referencing government-issued identification documents (e.g., passport, driver’s license) and company registration documents.
Customer Due Diligence (CDD):
- Building on the CIP, further understanding the customer’s background, occupation, nature of business, source of funds, and expected transaction patterns.
- Assessing the customer’s risk level (e.g., low, medium, high).
- For corporate customers, identifying and verifying their ultimate beneficial owners (UBOs).
Enhanced Due Diligence (EDD):
- For customers assessed as high-risk (e.g., Politically Exposed Persons (PEPs), customers from high-risk countries, or those in high-risk industries), more stringent and in-depth due diligence measures are required.
- This may include more detailed verification of sources of funds and wealth, understanding their business relationships, and obtaining approval from senior management before establishing a business relationship.
Ongoing Monitoring:
- KYC is not a one-time process; financial institutions need to continuously monitor customer transaction activities and risk profiles throughout the relationship.
- Regularly updating customer information to ensure accuracy.
- Monitoring transactions to ensure they align with the customer’s known business patterns and risk profiles, promptly identifying any anomalies or suspicious transactions.
7.3 Legal and Regulatory Framework of KYC
학습 목표: Recognize the main international and regional KYC/AML regulatory requirements.
The legal and regulatory framework for KYC/AML is multi-layered, encompassing international standards and specific legislation in various countries:
Overview of AML and CTF:
- AML: Refers to laws, regulations, and procedures aimed at preventing the laundering of illicit proceeds through the financial system.
- CTF: Focuses on preventing funds from flowing to terrorist organizations or being used for terrorist activities.
- KYC is a core element of AML/CTF compliance.
Financial Action Task Force (FATF):
FATF is an intergovernmental organization that sets international standards for AML/CTF. Its published “FATF Recommendations” are adopted as the legislative and regulatory basis by over 200 countries and regions globally.
- FATF recommendations explicitly require financial institutions to implement Customer Due Diligence (CDD, the core content of KYC), record-keeping, and suspicious transaction reporting measures.
- FATF has also issued specific guidance for virtual assets (such as cryptocurrencies) and their service providers (VASPs), mandating that VASPs comply with similar AML/CTF obligations, including conducting KYC.
Major Regulatory Requirements by Country (Overview):
- 미국: The Bank Secrecy Act (BSA) and its amendment, the USA PATRIOT Act, form the primary AML/KYC legal framework. The Financial Crimes Enforcement Network (FinCEN) is the main regulatory body.
- European Union: Implements unified AML/KYC standards through a series of Anti-Money Laundering Directives (AMLD, currently in its sixth version, AMLD6). The upcoming Markets in Crypto-Assets Regulation (MiCA) also imposes strict KYC requirements on crypto asset service providers.
- Singapore: The Monetary Authority of Singapore (MAS) imposes strict KYC/AML requirements on financial institutions and has extended these to digital payment token service providers.
- Other Regions: Most countries and regions have established their AML/KYC laws based on FATF recommendations.
7.4 Practical Application of KYC
학습 목표: Understand how businesses implement KYC processes and conduct risk assessments.
In actual operations, businesses typically combine policies, procedures, personnel, and technology to implement KYC processes:
KYC in Customer Onboarding Process:
- New customers must submit identification documents (e.g., ID card, passport, driver’s license) and proof of address (e.g., utility bills, bank statements) when applying for account opening or registration.
- Businesses verify these documents’ authenticity through manual review or automated tools, cross-referencing with blacklists, sanctions lists, and PEP lists.
- Biometric verification may include facial recognition and liveness detection (e.g., requiring a blink or head turn).
Risk Rating and Classification:
- Based on collected customer information (e.g., nationality, residence, occupation, industry, source of funds, expected transaction behaviors), and combining the business’s risk appetite and regulatory requirements, customers are risk-rated (e.g., low, medium, high).
- Risk rating determines the depth of subsequent due diligence and the frequency of monitoring. High-risk customers require stricter scrutiny and more frequent monitoring.
Using KYC Data for Compliance Decisions:
- Based on KYC results, businesses decide whether to establish a business relationship with customers.
- If a customer is found on a sanctions list or poses other significant risks, the business may refuse service.
- KYC data is also used to assess whether a customer’s transaction behavior aligns with their known background and risk profile to identify suspicious transactions.
Record Keeping:
- Businesses must properly retain all customer information collected during the KYC process, identity verification documents, risk assessment records, and transaction records in accordance with regulatory requirements. The retention period is usually at least 5 years after the end of the customer relationship.
Regular Review and Update:
- Regularly reassess the customer’s risk profile and update their KYC information, especially when significant changes occur in the customer’s personal situation or transaction behavior.
7.5 Technological Applications of KYC
학습 목표: Recognize how technology enhances the efficiency and accuracy of KYC.
Technology plays an increasingly important role in modern KYC processes, helping to improve efficiency, accuracy, and user experience:
Digital ID Verification Tools:
- Document Scanning and OCR: Using Optical Character Recognition (OCR) technology to automatically extract information from identification documents.
- Facial Recognition and Liveness Detection: Confirming identity authenticity by comparing selfies with document photos and requiring liveness checks (e.g., asking the user to blink or turn their head) to prevent photo or video fraud.
- NFC Chip Reading: Reading encrypted information from electronic passports or IDs with NFC chips for higher-level verification.
Application of AI and Machine Learning in Risk Analysis:
- AI/ML algorithms can analyze large volumes of customer data and transaction patterns to more accurately identify potential high-risk customers and suspicious transaction behaviors.
- Automated screening for negative news, sanctions list matching, and risk scoring based on preset rules and historical data reduce human error and increase risk identification efficiency.
Advantages of Automating the KYC Process:
- Enhanced Efficiency: Significantly reduces customer onboarding time from days to minutes.
- Cost Reduction: Decreases the workload and associated costs of manual reviews.
- 향상된 사용자 경험: Provides a more seamless and convenient account opening experience.
- Increased Consistency: Standardized automated processes reduce discrepancies in subjective human judgments.
- 확장성: More easily accommodates the KYC demands of large volumes of customers.
Database and API Integration:
- Integrating various external databases (e.g., government databases, business information repositories, sanctions lists, PEP lists, adverse media information) for real-time querying and verification.
Blockchain and Decentralized Identity (DID):
- In the future, blockchain-based decentralized identity solutions may offer new pathways for KYC, allowing users to better control their identity data and securely authorize verification to service providers while protecting privacy.
7.6 Challenges in Implementing KYC
학습 목표: Identify common difficulties in executing the KYC process.
High Compliance Costs:
- Implementing and maintaining KYC systems requires significant investment, including technology procurement, personnel training, database subscriptions, and manual reviews. Reports indicate that large financial institutions may spend tens of millions of dollars annually on KYC compliance.
- Inefficient KYC processes may also lead to customer attrition and revenue loss.
Data Source Integration and Quality Issues:
- Effective KYC relies on accurate, complete, and timely data. However, data may be scattered across different internal systems and external databases, making integration challenging.
- The quality of external data sources can vary, potentially containing errors, outdated, or incomplete information, which affects the accuracy of risk assessments.
- Different countries and regions have varying formats and data standards for identification documents, increasing verification challenges.
Rapidly Changing Regulatory Environment:
- AML/KYC regulations are continuously updated and evolving, requiring businesses to invest resources to track and adapt to new regulatory requirements and adjust their policies and processes.
- Multinational enterprises must also navigate different regulatory requirements across jurisdictions.
Balancing Compliance and User Experience:
- Overly cumbersome or lengthy KYC processes may lead to poor user experiences and increased customer dropout rates.
- Businesses need to simplify processes while meeting strict compliance requirements, and technology can help achieve this balance.
Threat of Forged Documents and Identity Fraud:
- Criminals continually employ more sophisticated methods to forge identification documents or commit identity theft, posing challenges to KYC verification technologies and manual review capabilities.
Data Privacy Protection:
- The KYC process involves collecting and processing large amounts of sensitive customer personal information. Businesses must comply with strict data privacy regulations (e.g., GDPR) to ensure data security and prevent breaches.
Identification and Management of High-Risk Customers:
- Accurately identifying and effectively managing high-risk customers (e.g., PEPs, customers in sensitive industries) requires specialized knowledge and resources.
7.7 Specificity of KYC in the Digital Asset Industry
학습 목표: Understand the challenges and practices of KYC in the digital asset industry.
The digital asset industry (e.g., cryptocurrencies) presents new challenges to traditional KYC practices due to its anonymity, decentralization, and globalization, while also driving the development of corresponding solutions:
Challenges of Anonymity and Pseudonymity:
- Blockchain transactions are typically associated with pseudonymous addresses rather than real identities, making it more challenging to trace the flow of funds and identify the true identities of transaction participants.
- While blockchain analysis tools can assist in tracking fund movements, linking on-chain addresses to off-chain identities is key to KYC.
Global Operations and Cross-Border Compliance:
- Many cryptocurrency exchanges and service providers (VASPs) operate globally, needing to comply with KYC/AML regulations across multiple jurisdictions, which may have differing or conflicting requirements.
- FATF’s “Travel Rule” requires VASPs to obtain and transmit relevant information about the sender and recipient during virtual asset transfers, raising KYC demands for cross-border transactions.
Challenges of Decentralized Services:
- For decentralized exchanges (DEXs) and DeFi protocols, implementing effective KYC is a challenge due to the lack of centralized operational entities.
- Regulators are exploring how to oversee these decentralized entities.
KYC Requirements for Exchanges and Wallet Service Providers:
- Most centralized cryptocurrency exchanges (CEXs) now require users to complete various levels of KYC verification to utilize their services (e.g., trading, withdrawals).
- Some non-custodial wallet service providers are also exploring how to offer compliance-friendly identity verification options while protecting user privacy (e.g., collaborating with third-party KYC providers).
Application of Emerging Technologies:
- Blockchain analysis companies (e.g., Chainalysis, Elliptic) provide tools to help VASPs analyze transaction risks and identify addresses associated with illegal activities.
- Technologies like decentralized identity (DID) and verifiable credentials (VCs) have the potential to provide more secure, efficient, and user-friendly KYC solutions in the digital asset industry.
Evolution of Regulation:
- Regulatory bodies are striving to keep pace with the rapid developments in the digital asset industry, continuously updating targeted KYC/AML guidelines and regulations.

